September 26, 2025
Incident Response6 min. read
6 Cyber Security Incident Response Steps: Practical Plan Against Attacks
Cyber attack incident response plan costs pennies compared with downtime. Automation closes gaps that human eyes miss. Adaptive AI like Nothreat’s evens the odds for resource‑strapped teams.

Mastering incident response: a step-by-step guide for resource-constrained cyber security teams
Every business runs on digital trust. But the moment an attacker lands in your network, a clock starts ticking. For enterprises, a well-rehearsed incident response plan is what makes a difference between a misstep and a headline cybersecurity breach.
In this guide, we demystify the cyber security incident response, show how new self-learning defences fit into the picture and where adaptive AI from Nothreat can support your business.
Why should you care
Small or large, your business may not make front page news (yet), but the data you handle is valuable, making you a lucrative target. For example, 48% of small and medium businesses have experienced a cyberattack, yet 43% struggle to understand what kind of security they need.
The cost of cybercrime is predicted to grow from $8.4 trillion in 2022 to $23 trillion in 2027. Even a tiny fraction of that figure can wipe out a major part of profit. Based on that, an incident response plan seems less a luxury than a necessity.
How does threat landscape look in 2025
Ransomware surge
Attackers favour tactics that (quite literally) pay quickly. Ransomware accounted for 70% of Sophos Incident Response for small businesses, and over 90% for medium-size companies.
AI-powered phishing
Phishing emails allow intruders to easily put a foot in the door of your security. Astonishingly, phishing attacks increased by 4151%since ChatGPT was launched.
Vulnerability shortcuts
Why waste time crafting an attack when a missed patch opens the door? Analysts report a 34% increase in cybercriminals exploiting existing vulnerabilities to gain initial access.
When a vulnerability becomes known, a hostile code can appear within hours. Without an incident management plan, even well-tooled IT teams risk paralysis. Combining industry standards (including the NIST Computer Security Incident Handling Guide) and our expertise, we have put together a step-by-step plan, adapted for lean headcount.

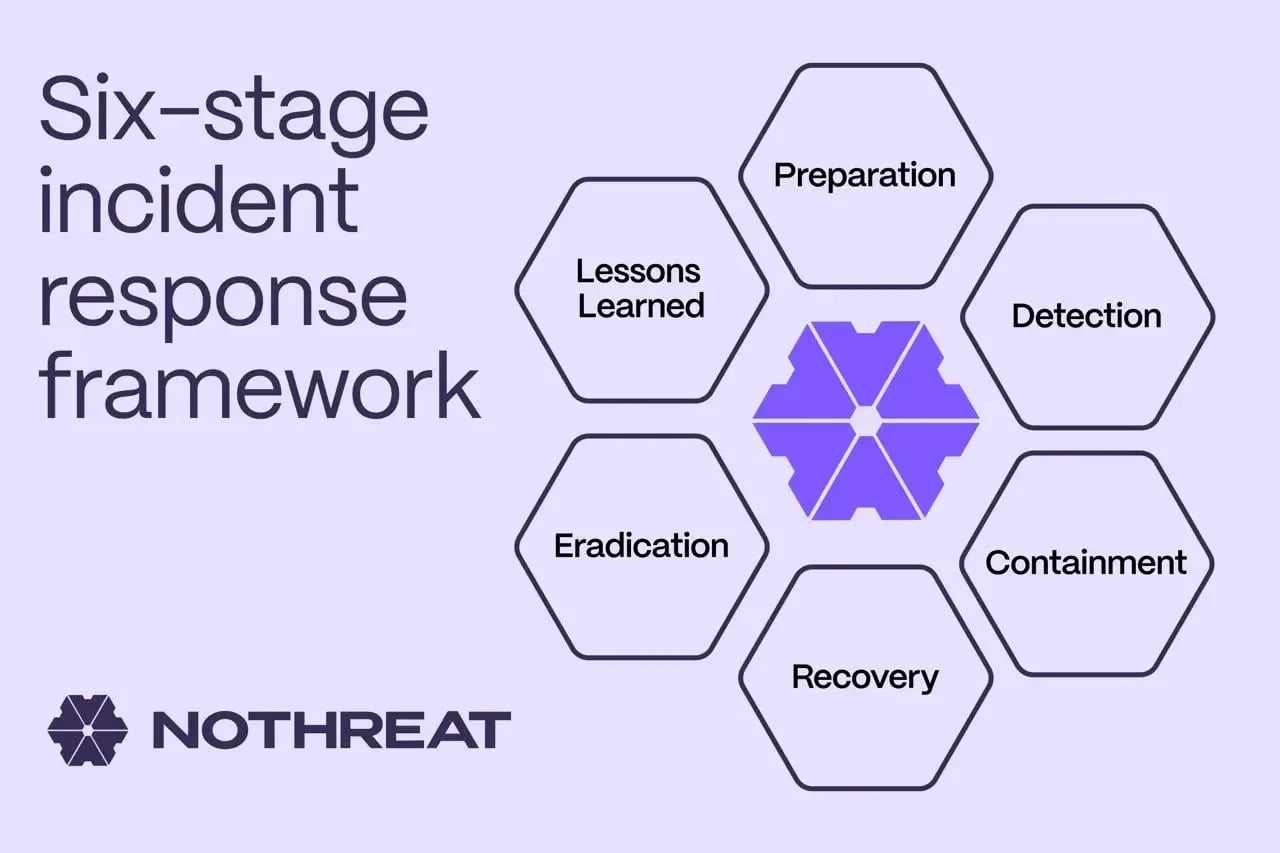
Six cyber security incident response steps
1. Preparation – map assets and roles
- List on–premises, cloud and edge assets, then rank them by business impact, creating an asset map.
- Nominate decision–makers, technical leads, legal counsel and a single external voice.
- Run drills and live red–team events twice a year to test muscle memory.
Where Nothreat can help: our platform’s discovery module sweeps the estate and automatically labels new threats, filling gaps that sabotage tabletop accuracy.
2. Detection – monitor signals, not noise
- Collect and unify logs, firewall and endpoint events and threat intel into a single lake.
- Flag behavioural anomalies - for example, a payroll system connecting to Tor.
- Triage alerts by criticality within five minutes.
Nothreat benefit: the platform’s self–learning models track traffic patterns in real time and surface true positives with a false–positive rate below 1%, giving analysts back the precious time.
3. Containment – isolate the threat
- Use automated detection and response systems that can distinguish real threats from noise with minimal false positives.
- Deploy network-level containment to immediately block malicious traffic without impacting legitimate business activity.
- Leverage deception technology to redirect attackers into decoys, preventing them from accessing critical assets.
- Isolate services if they are seriously breached
- Use automated solutions with a low false-positive rate.
Role of Nothreat: momentarily enforcing your firewalls with AI to cut off malicious connections within milliseconds, even when a site–to–site VPN link is saturated.
4. Eradication – remove the root cause
- Apply fixes or software patches to exploited services.
- Re–image, rebuild or surgically clean systems while verifying supply–chain integrity.
- Hunt for scheduled tasks, rogue services and web shells.
- Verify supply chain - check third-party libraries and container images for potential loopholes.
Nothreat use case: deception tokens lure attackers, making eradication validation easier. We set up beacons both within and outside the perimeter to capture the attacks early.
5. Recovery – clean, test, restore
- Restore from trusted backups and verify hashes before restoration.
- Phase return–to–service - stagger bringing systems online to spot anomalies.
- Inform regulators and customers.
Nothreat in action: once beacons go silent within the security perimeter, you know persistence is gone.
6. Lessons learned – feed the loop
- Hold a review within 72 hours - focus on learnings, not finger-pointing.
- Track detection–to–containment time and unplanned downtime.
- Update playbooks and integrate lessons into the next drill.
Where Nothreat helps: our reporting engine automatically generates a human–readable timeline, complete with MITRE ATT&CK mapping.
Incident response trends to watch
Three shifts are defining the future of incident response and management.
- Speed over size – attack chains compress. AI-enabled attackers probe many targets at once, forcing defenders to automate decisions.
- Hybrid teams – internal security and managed service providers share playbooks to cover gaps.
- Built-in deception – lightweight decoys inside networks detect lateral movement early.
Solutions like Nothreat Platform (CTEM) and Nothreat CyberEcho constantly apply AI-powered threat analysis to enhance the real-time battle against intruders. With continuous learning and patent-pending CyberEcho technology, they enable incident response teams with the most intelligent and up-to-date cyber defense knowledge base.
The result? Instant response to zero–days without endless signature update and continuous self-tuning. Crucially, the platform explains its verdicts in plain English – helpful when a finance director demands an overnight incident report.
In practice, AI augments rather than replaces human expertise. It shortens dwell time and lets analysts focus on strategy rather than swivel-chair investigations.
An incident does not need to become a crisis. With a clear plan, rehearsed roles and adaptive AI tech, businesses can spot trouble early, clear it out quickly and learn enough to avoid the sequel.
FAQs
Is incident response orchestration the same as incident management?
Not quite. Incident response covers the urgent technical actions. Incident management stretches from preparation to ongoing improvement and governance.
Where should we start if we have no incident response plan at all?
Start with a one-page plan: name an incident lead and deputies; list critical systems, data owners and after-hours contacts; agree severity levels and first actions (isolate a host, disable accounts, preserve logs). Put basic monitoring, secure backups and a shared “war room” channel in place. Run a 30-minute tabletop to test the flow and revise. If resources are tight, line up an external incident-response partner and add their 24/7 contact.
How often should we test the plan?
Aim for at least one live exercise and two tabletop sessions each year, plus after any major infrastructure change.
Will cyber insurance replace an incident response plan?
Insurance may cover some costs, yet most policies require strong evidence of due diligence – including a maintained incident response plan.
Can AI really detect a brand‑new exploit?
Yes. Behaviour‑based models spot deviations rather than relying on known signatures, giving you protection before patches land. It lowers mean time to recovery and reduces overtime hours that drive costs up.
How does incident response reduce cost after a breach?
Early discovery and separation reduce downtime, inhibit malware propagation and reduce recovery costs - or even ransom payments. Seamless incident response also assists with insurance claims and compliance with regulators, lowering long-term risk.