December 12, 2025
Vulnerabilities4 min. read
What to Do When a Known Vulnerability is Being Exploited
When a known vulnerability turns into an active exploit, teams must act fast: confirm exposure, apply stopgap controls, hunt for intrusion and patch immediately—rotating keys and tightening perimeter defences to shut attackers out. The article stresses preparation through asset accuracy, rehearsed response and layered security. With adaptive, self-learning protection like NoThreat, organisations gain crucial breathing room even as zero-day exploitation windows shrink.

Checklist: What to Do When a Known Vulnerability is Being Exploited
Picture this: you’re making a morning cup of tea when your phone buzzes with alerts. At first you think it’s a colleague looking for a password or an update on a ticket. You look down, and your stomach drops. A loophole you read about yesterday has turned into a foothold for cybercriminals. It’s no longer a theoretical risk in a long list of CVEs (common vulnerabilities and exposures) – it’s happening to you.
In order to help you speed up deflecting malicious requests, we’ve created a checklist for businesses to act confidently the next time a known vulnerability is being exploited.
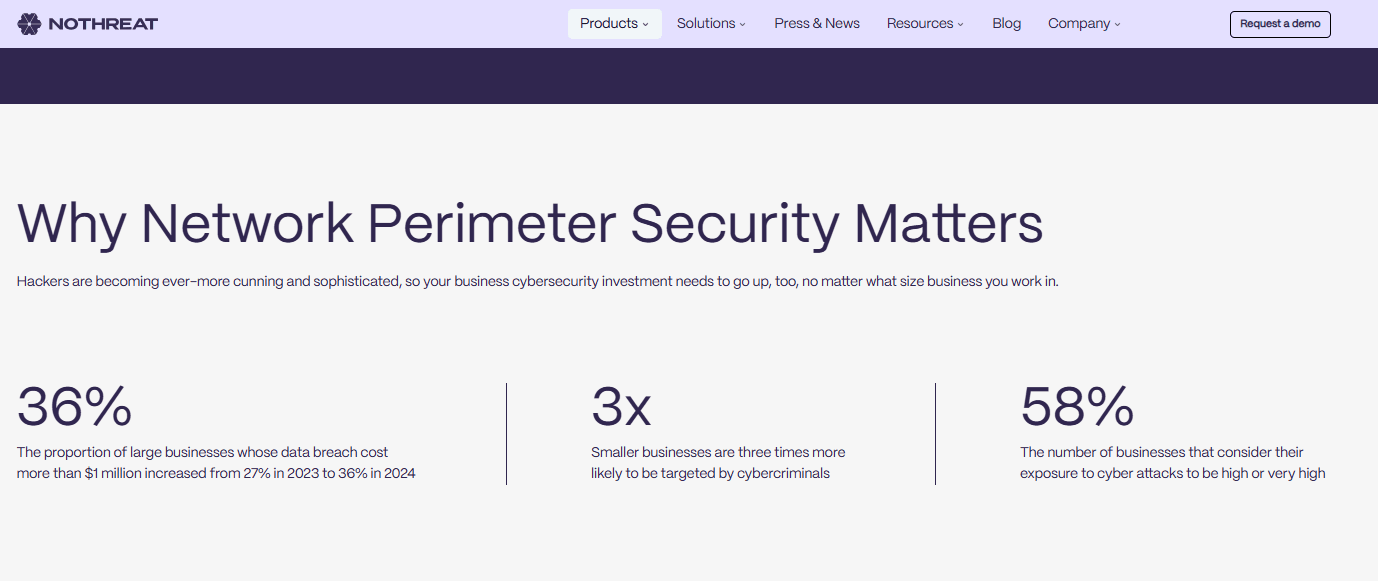
Why you need to move fast
Zero-day attacks are a major headache for any security team - and the exploitation windows keep shrinking. Google’s threat research found 75 zero‑day vulnerabilities were exploited in 2024. During the recent Pwn2Own Ireland 2025 hacking competition, security researchers collected $792,750 in cash after exploiting 56 unique zero-day vulnerabilities in a day. Major corporations like Cisco, Oracle, Samsung and others face the issue every day.
Zero-day bugs spread widely and quickly. In an example of an exploited vulnerability in Microsoft SharePoint, within days, attackers were stealing cryptographic keys and executing arbitrary commands. Even though Microsoft were quick to react and the patches were released swiftly, organisations that failed to rotate machine keys found intruders still operating. Lesson learned? Don’t underestimate any flow, however niche it may seem.

A calm approach: ask the right questions
It’s tempting to throw the kitchen sink at a problem when panic sets in. Instead, we recommend stepping back and going through the checklist questions below. These will guide your response and keep you from wasting time.
1. Are we in the blast radius?
Are only onpremises versions exposed, or does it affect online services? Create or consult your asset inventory and confirm you’re running the vulnerable product and version.
2. What levers can we pull?
Stopgap measures often exist. Limiting access to management interfaces and disabling certain components is often enough to halt most attacks until a patch is released. These actions aren’t fancy, but they buy breathing room.
3. What windows are still open?
Even if you aren’t an immediate target, check your perimeter. Turn off services you’re not actively using, enforce multifactor authentication and restrict inbound traffic to those who really need it.
4. Has anything been compromised?
Finding evidence of unusual activity can feel like playing detective. Look for outliers and focus your search.

Deploying patches and securing persistence points
Even if the emergency patches are issued, without rotating keys, systems remain vulnerable to session hijacking.
Your remediation plan should include:
- Installing patches to cut off active exploitation, with priority given to business-critical systems.
- Changing credentials to prevent attackers continue on patched systems by using stolen machine keys.
- Reinforcing endpoint defence, including antivirus, AMSI, and EDR tools being active and scanning in real time.
How can Nothreat help?
If you’ve ever wondered how some companies breeze through cyber incidents that flatten others, it’s all about being prepared. Nothreat technology combines behavioural analysis with deception techniques, adapting within minutes – long before traditional signatures are updated. It’s like having a guard who not only recognises faces but also notices when someone is moving in an unusual way.
For businesses, this matters. Banks, insurers, telecoms and IoT device makers can’t afford prolonged outages or reputational damage. While a traditional security can falter against a major security flaw, a self‑learning defence like the one by Nothreat buys time and reduces the pressure, meaning zero downtime.
Preparing for the next time
We can’t predict every attack, but we can prepare for vulnerabilities being exploited.
- Keep an accurate asset list. Knowing what you have makes it much easier to answer “are we affected?”
- Prioritise updates. Schedule regular times to apply patches and firmware updates, especially on internetfacing systems.
- Practise your response. Run through tabletop exercises so that roles and decision-making lines are clear. It’s less stressful to make mistakes in a simulation than when under pressure from live attackers.
- Layer your defences. Use a mix of signaturebased and behavioural tools.
A vulnerability that’s already being exploited is a test of your processes and your technology. Confirm whether you’re at risk, apply temporary measures, harden your perimeter and hunt for signs of intrusion. When a fix is released, patch promptly - then reflect on what worked and what didn’t. You can’t control when the next bulletin arrives, but you can decide to be ready.
An incident does not need to become a crisis. With a clear plan, rehearsed roles and adaptive AI tech, businesses can spot trouble early, clear it out quickly and learn enough to avoid the sequel.

FAQs
What is a zero‑day attack?
It’s an exploit of a vulnerability before the vendor has released a fix. A zero‑day exploit leaves no time for traditional signature updates.
Should I wait for evidence before patching?
No. Install the patch as soon as possible and investigate in parallel. Delaying leaves the door open longer.
What if I can’t patch right away?
Follow vendor recommendations: disable vulnerable features, restrict access and monitor closely. These measures reduce risk while you plan for a maintenance window.
Do exploited vulnerabilities happen often?
More often than many people think. Planning for active exploitation prepares you for the inevitable.